02. Disk Encryption / Data Security / Privacy
2 of 24 free services/ Software to ease our life:
I’ve been using this divine Free Open-Source On-The-Fly Disk Encryption Software for Windows Vista/XP, Mac OS X and Linux for about 4 years now! And you know what, I never did suffer a single privacy threat since the day I started using this disks encryption and data security software! I strongly recommend you to read the TrueCrypt User Guide before you decide to use this blazing encryption tool though I found it extensively user friendly and intuitive. Latest version is TrueCrypt 6.1a released on December 1, 2008. Main features of TrueCrypt include:
- Creates a virtual encrypted disk within a file and mounts it as a real disk.
- Encrypts an entire partition or storage device such as USB flash drive or hard drive.
- Encrypts a partition or drive where Windows is installed (pre-boot authentication).
- Encryption is automatic, real-time (on-the-fly) and transparent.
- Provides two levels of plausible deniability, in case an adversary forces you to reveal the password:
1) Hidden volume (steganography) and hidden operating system.
2) No TrueCrypt volume can be identified (volumes cannot be distinguished from random data). - Encryption algorithms: AES-256, Serpent, and Twofish. Mode of operation: XTS.
Further advanced information regarding features of this software may be found in the documentation provided bay the publisher’s site . Some may have a look in the TrueCrypt FAQ before stepping ahead.
Step-by-step How to Use:
Download the latest release from publisher’s site. Run the TrueCrypt Setup X.xx.exe and you’ll be promoted to how you would like to install (registry installation or portable -i.e. just extract). You can directly download the portable version 6.1a from my box.net sharing also. Run the TrueCrypt.exe and follow the instruction. If you have read or at least skimmed through the User Guide, you good enough to be on your own. Otherwise stop right here and first finish reading the guide, even if you never read FAQ or any user guide. OK?! Now follow the pictorial depiction below:
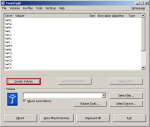
Step-01:Create Volume
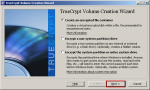
Step-02:Volume Creation Wizard
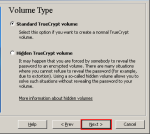
Step-03:Volume Type
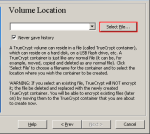
Step-04:Volume Location

Step-05:Volume Name

Step-06:Volume Location
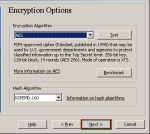
Step-07:Encryption Option
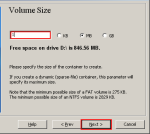
Step-08:Volume Size
Step-09:Volume Password
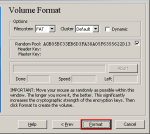
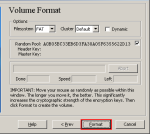
Step-10:Volume Format
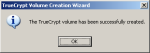
Step-11a:Volume Creation Wizard
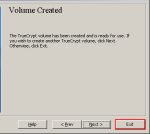
Step-11b:Volume Created
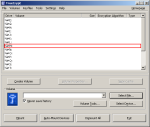
Step-12: Drive Mount-select drive letter
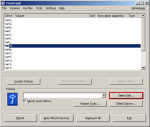
Step-13: Drive Mount-select file (TrueCrypt container)
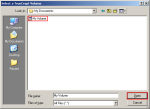
Step-14: Select TrueCrypt volume
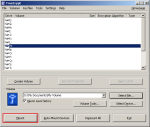
Step-15: Drive Mount
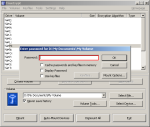
Step-16: Drive Mount-enter password
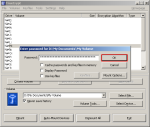
Step-17: Drive Mount-password confirmation
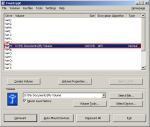
Step-18: Volume Mounted in TrueCrypt
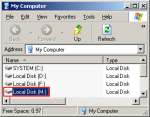
Step-19: Volume Mounted in Explorer

Step-20: Dismount Drive
Now guys, You just have created an encrypted volume or you can name it a drive in plain English. Use the drive as you use any other drive in your windows or Mac or Linux, whatever you use. I used here the windows XP OS screen shot since most of the user’s gonna use TrueCrypt in Windows. I’m personally using this divine software in my Ubuntu OS too. I didn’t try to show you the multimedia presentation here on how to use TrueCrypt, rather I tried to show you the total process in a nutshell. And believe me: I hate using too much image in my blog, still I did it for you. So, those who are my type- plz frogive me and those who found it helpful and opt for a clearer depiction:- PLZ, read the UserGuide &/or FAQ; esp: Screenshots@ publisher’s website.
The fact is , you have several option to explore if you actually need those advanced features like Hidden volume i.e. steganography, using keyfiles along with passwords etc. My advice is to make the TrueCrypt file as System file and Hidden File from the Command prompt. That way you can hide the content of your Encrypted volume along with the container file also!
And let me know if you want to know anything details or facing any problem. Actually that chance has a least remote possibility since the software is extremely user friendly and the user guide is elaborative. Most of all- you know, there’s nothing in this world you can’t fingd Googling! And Guys like Devin Knighton of Mozy- I don’t need your appreciation, not even your silly Thanks man! You people try to commercialize everything in your way.. I hate that! Again I say, I’m a True Believer of Open Source Philosophy. And I’m glad that this TrueCrypt Software is one of them!